

I was recently interviewed by a specialized cybersecurity magazine regarding my view on the evolution of some aspects of cybersecurity in 2022. I would like to share these thoughts with you, because the need for adequate cybersecurity exists more than ever.
The following topics are handled in this post:
As expected, the number of attacks increased in 2021 in comparison with the previous years, and is expected to further increase in 2022. In 2021 the number of successful ransomware attacks increased, and some of these even made the mainstream media. Ransomware attacks are attempts to take an organisation hostage, by encrypting all of its data. The cybercriminals try to sell the keys to decrypt to their victims, in some cases for large amounts of money. In Belgium, we’ve seen such successful ransomware attack amongst others in Mediamarkt, a consumer electronics retailer.
Next to ransomware attacks, we’ve seen a lot of phishing attempts, becoming more and more sophisticated. Phishing is a type of social engineering where an attacker sends a fraudulent message designed to trick a human victim into revealing sensitive information such as passwords or banking details to the attacker. Phishing was in 2021 also the main method of planting ransomware into the network of an organisation. The aim of phishing is either to steal money directly, or to blackmail a person or organisation.
At the end of 2021, we’ve seen another emerging threat. Hackers were able to execute code on an apparently harmless backend server. I’m talking about the log4j vulnerability that was discovered beginning of December. Exploiting such vulnerabilities (which are at the time of writing this document not yet discovered) will most likely become a new threat in the coming years. Such vulnerabilities enable the hackers to plant and execute ransomware without the need of human intervention such as clicking on an E-mail in the targeted organisation. Defence in Belgium was hacked using the log4j vulnerability rendering parts of its network useless for a couple of days.

Figure 1 - Ransomware nightmare
Another category of attacks we see are the so-called "denial of service" attacks. The goal of such attack is to bring the systems of the targeted organisation offline for all sorts of reasons, such as political or religious reasons. In early 2021, some websites of the Belgian were taken offline by distributed denial of service attacks.
Another worrying event in 2021 was the hacking of Kaseye. Cybercriminals planted ransomware in the automatically installed updates of a Kaseye security product, flooding hundreds of companies with ransomware within a matter of hours.
2021 is also the year in which the attacks on smartphones significantly increased. In Belgium, the telecom providers had to block 2 million SMS phishing messages per day in early September. These messages attempted to install the Flubot virus on the smartphones, giving the attackers control over the device and enable them to access the wallets and the bank accounts installed on these smartphones.
Unfortunately, more of the same. The last few years were record-breaking years, so was 2021.
There is some improvement regarding awareness, but the cybercriminals are still some steps ahead, and they get better and better organised.

Figure 2 - Mobile devices under attack
As mentioned, there are some new emerging threats. Cybercriminals no longer need human action in the targeted organisation to launch ransomware and hold the organisation hostage. New vulnerabilities enabling the automated distribution and executions of ransomware will most likely be found. One can expect that malicious organisation are focussing their research on the discovery of such vulnerabilities.
In 2022, the smartphone will also play an increasingly important role in cyber criminality.
There is not just one cause. It is a combination of various causes, all of major importance. It is difficult to give a ranking to these causes, because every situation is different.
The first cause of the increasing number of successful attacks is that hacking is a very lucrative business, hackers are getting more and more organised in big organisations earning a lot of money. The availability of funds enables these cyber criminals to further develop their malicious techniques and technologies. Money is the most significant driver.

Figure 3 - Hacktivism
Hacktivism is a second cause. Political, social, religious and anarchist activists more often use Cyber criminality techniques to make their voice heard and expose what they believe is unjust.
Lack of awareness concerning cyber safety, not only of the public, but also of the professionals fulfilling critical roles in all types of organisations is also a major cause. Lack of awareness of the people enables hackers to perform their malicious activities. These days people have to be alert and vigilant all the time.
Another important cause is the lack of good and performant security management processes in companies and other institutions. What we see is that people put a security control in place, and get a false sense of being protected. My motto regarding security is that security is a process. The vulnerability landscape evolves, so do the hacking techniques. It is only logical that the defence lines continuously need to be adopted to the continuously evolving threat landscape.
There is a lack of cybersecurity awareness on all levels in most organisations. Let’s focus on the cybersecurity approach for instance. In all types of organisations, security must be driven by the business. In most cases we see however that security is handled by technical ICT departments, under the control of the CIO. This is wrong.
Security, including cybersecurity should be a recurring topic on the agenda of the corporate governance. The goal of cybersecurity is to protect the company assets, whatever they are. The approach should be risk based. I’ll try to briefly clarify what I mean.
All business processes with their accompanying supporting capabilities (and these are not only ICT capabilities) should be inventoried. The various threat scenarios should be identified and prioritised according to impact in case of an events (breach) in combination with the likelihood of events.
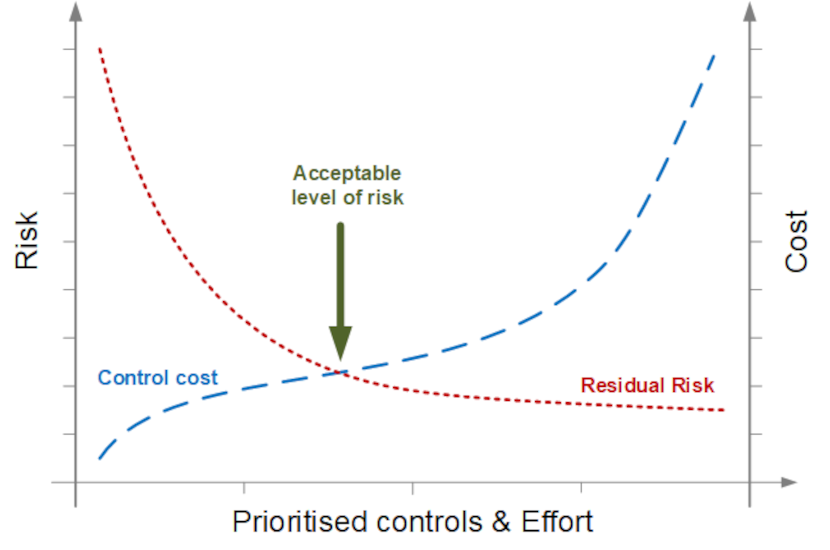
Figure 4 - Acceptable level of risk
Such risk analysis or business impact analysis should lead to a clear view in the annual financial loss expectancy. On top of the prioritised list of threat scenarios we’ll find the scenarios with the largest expected financial impact. It is obvious that these should be analysed first and counter measures (security controls) protecting the supporting capabilities of the business processes should be put in place accordingly.
In reality the process is a bit more complicated that what I explain now, because there is not necessarily a one-to-one relation between a threat (or risk) scenario and a security control.
It is important however that the cost of the security controls does not exceed the amount of the residual risk. In any case, the decision whether or not to implement security controls, is a decision that should be taken by the business, rather than the ICT departments.
For the broad public, the focus should be on awareness and training, people should understand that cybersecurity should be on top of their mind whenever they use online devices such as smartphones and laptops.
The awareness is definitely increasing, but the results of a global phishing campaign in October 2021 were still not good. In this campaign, one million phishing E-mails were sent to end-users. 19.8% of the total participants clicked on the phishing E-mail link, 14.4% of the participants downloaded the malicious document in the phishing simulation webpage. These figures show that phishing is still a very lucrative business for the attackers.

Figure 5 - Security Awareness
The mindset of the people should be that if something looks like phishing, it almost certainly is. Don’t fall for it. Be careful and alert at all times.
For organisations, there should be a shift in the responsibilities. (Cyber)security should be a recurring process that is run by the corporate governance rather than the technical IT departments. Identify the threats, quantify the risks and prioritise the controls. Cybersecurity should support the business, not the other way around...
I would like to stress again on the fact that security is a process, not a onetime project, because, as soon as the project is finished, the level of protection starts to drop.
Yes, I would like to end with some figures:
The average cost of a data breach or other cybersecurity related incident in a SME (<500 employees) adds up to over 2 million EURO.
Over 60% of the smaller organisations go bankrupt within 6 months after being hit by a cyberattack.
About 1 in 300 E-mails is a targeted malicious E-mail.
These figures don’t lie. Be safe!
That's it! I hope you enjoyed reading this post. Feel free to contact me in the case of comments and/or questions.
The illustrations were taken from pixabay, except figure 4, I drew that one myself.
January 2nd, 2022 by Tom Snauwaert.